
Jake | JCyberSec_@JCyberSec_
Nov 24, 2022
17 tweets
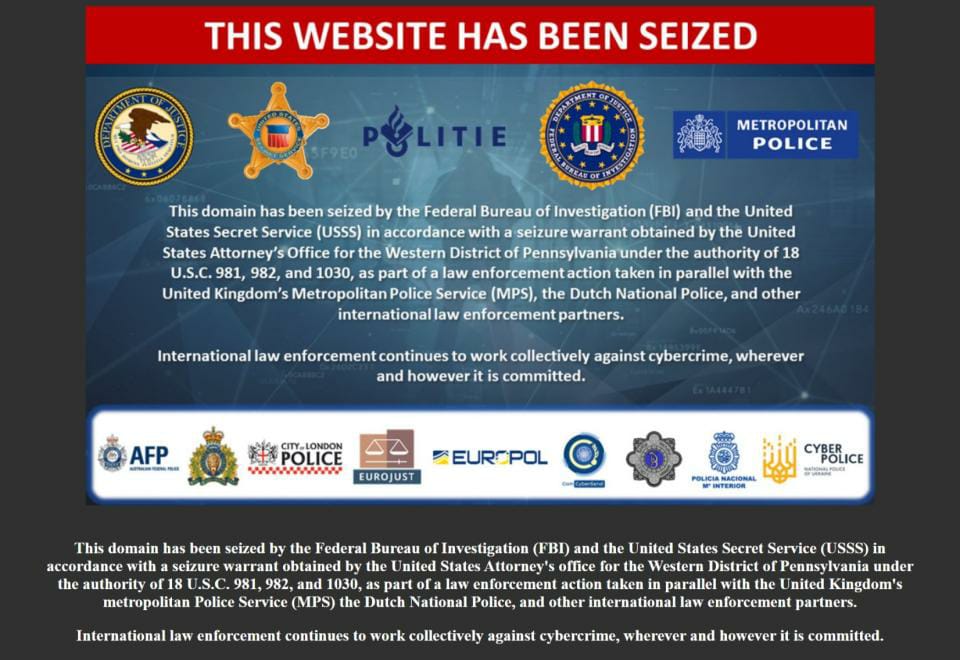
 UK police to send 70,000 SMS after taking down ispoof
The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc
UK police to send 70,000 SMS after taking down ispoof
The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc Full Details and Analysis in Thread
Full Details and Analysis in Thread

 UK police to send 70,000 SMS after taking down ispoof
The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc
UK police to send 70,000 SMS after taking down ispoof
The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc Full Details and Analysis in Thread
Full Details and Analysis in Thread

 UK law enforcement are now preparing to send 70,000 SMS messages to potential victims of the site
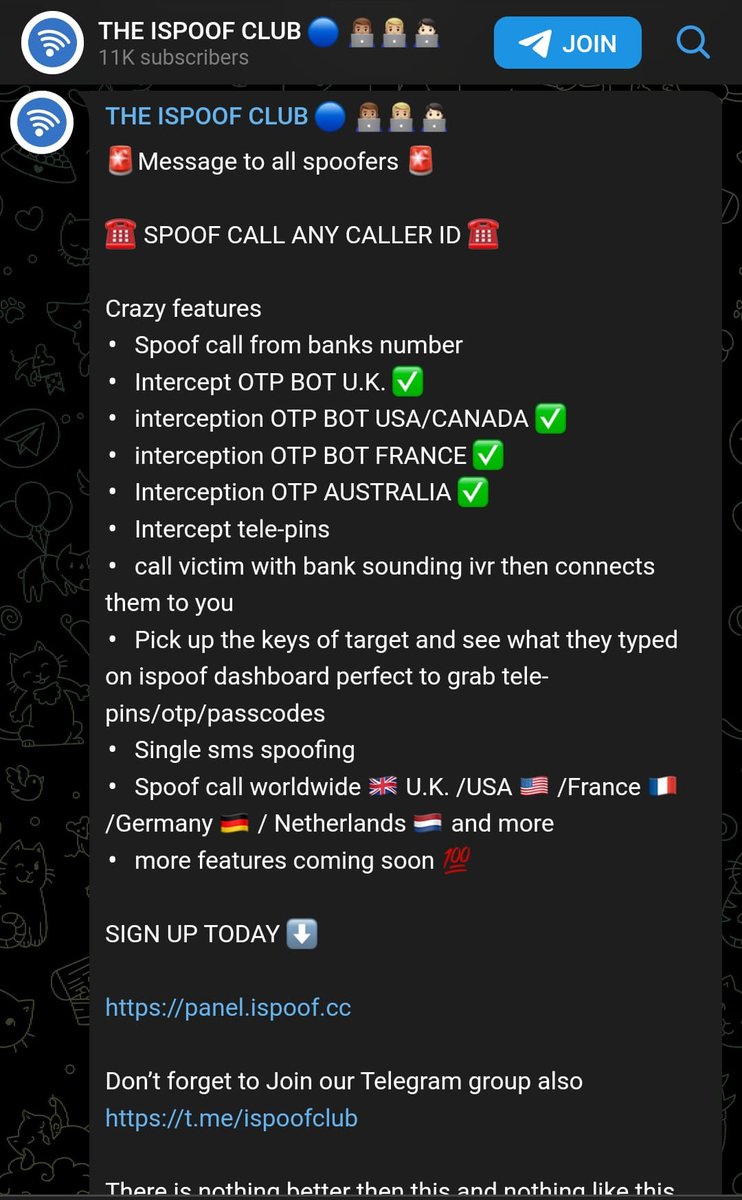
ispoof allowed controlling users to intercept OTP and Telepins of victims
UK law enforcement are now preparing to send 70,000 SMS messages to potential victims of the site
ispoof allowed controlling users to intercept OTP and Telepins of victims 



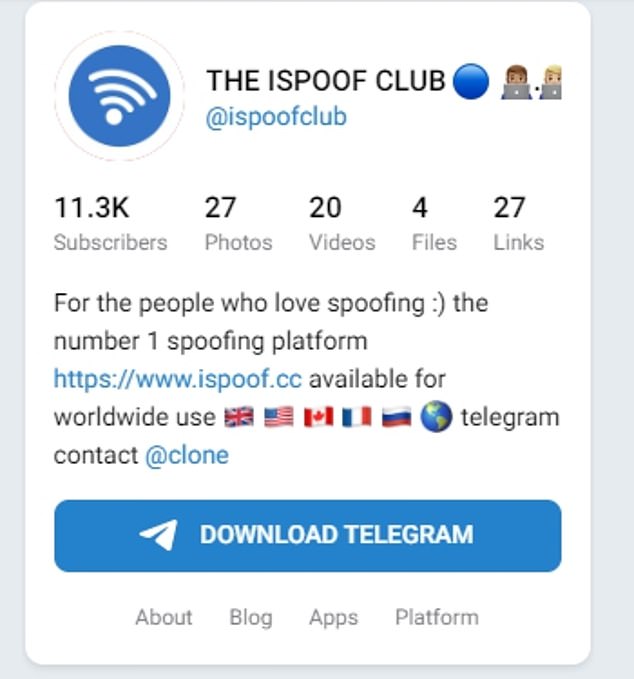
 This video was uploaded to the ispoof telegram channel and is beyond amazing!!!
This video was uploaded to the ispoof telegram channel and is beyond amazing!!! 



 Alleged site administrator Teejay Fletcher, 35, has been arrested and charged with making or supplying articles for use in fraud and for participating in the activities of an organised crime group
Alleged site administrator Teejay Fletcher, 35, has been arrested and charged with making or supplying articles for use in fraud and for participating in the activities of an organised crime group
 Here is the 'original' marketing video ispoof created...
Here is the 'original' marketing video ispoof created...  ispoof was created in December 2020 and at its peak had 59,000 users, allowing them to pay for the criminal software using Bitcoin, with charges ranging from £150 to £5,000 per month
ispoof was created in December 2020 and at its peak had 59,000 users, allowing them to pay for the criminal software using Bitcoin, with charges ranging from £150 to £5,000 per month
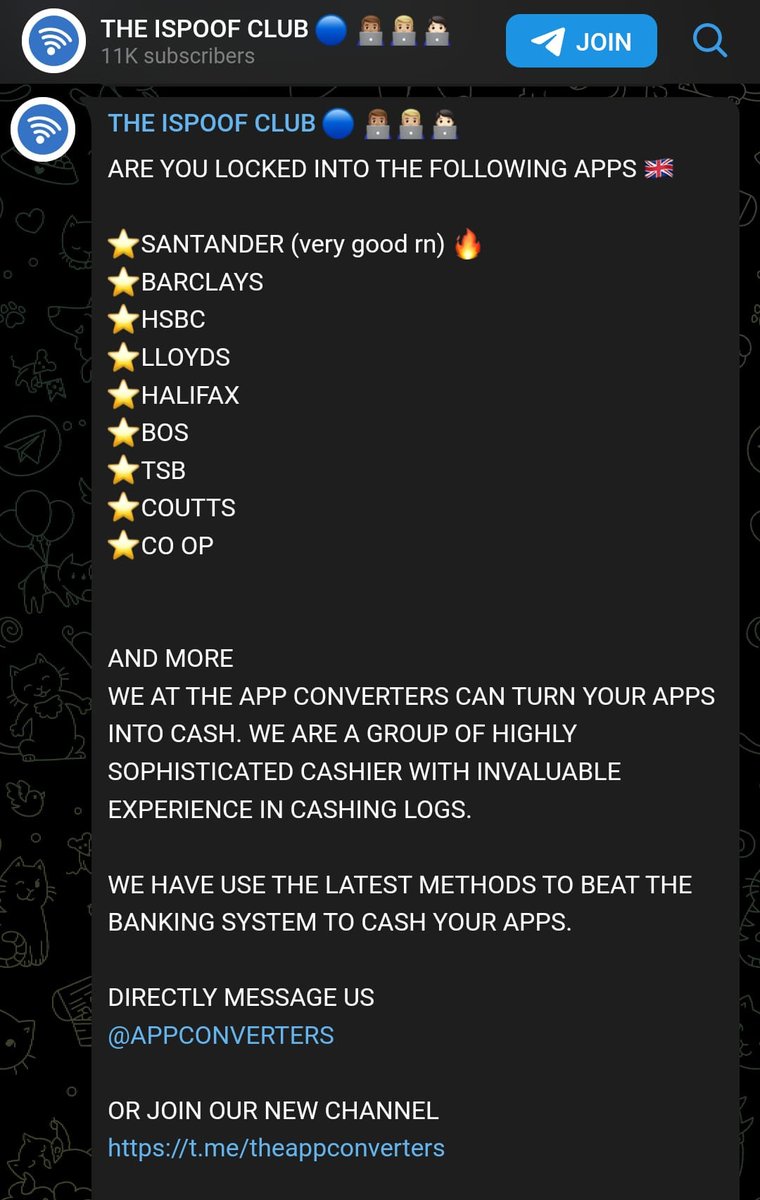
Threat actors paid a subscription to iSpoof.cc to use technology that let them appear as though they were phoning victims from banks such as Barclays, NatWest and Halifax

Of 10 million fraudulent calls made, 40% were in the US , 35% were in the UK
, 35% were in the UK and the rest were spread across other countries
and the rest were spread across other countries So far 120 arrests have been made in the UK alone
So far 120 arrests have been made in the UK alone

 , 35% were in the UK
, 35% were in the UK and the rest were spread across other countries
and the rest were spread across other countries So far 120 arrests have been made in the UK alone
So far 120 arrests have been made in the UK alone

 On Thursday and Friday, around 70,000 UK phone numbers called by criminals who used the site will be alerted by the Metropolitan Police via text message and asked to contact the force.
However, if a text message comes after that time, it will not be from the force
On Thursday and Friday, around 70,000 UK phone numbers called by criminals who used the site will be alerted by the Metropolitan Police via text message and asked to contact the force.
However, if a text message comes after that time, it will not be from the force
 Dutch law enforcement managed to inject a tap onto the website's servers in the Netherlands to intercept the phone calls allowing them to record the calls and recover numbers of incoming and outgoing calls
Dutch law enforcement managed to inject a tap onto the website's servers in the Netherlands to intercept the phone calls allowing them to record the calls and recover numbers of incoming and outgoing calls
Analysis Time
 Any LE action is positive. Disruption is key to preventing fraud and scams from taking over. Although this website has scammed a huge number of people and any actors not arrested after this action will just move to another spoofing service this is good to see
Any LE action is positive. Disruption is key to preventing fraud and scams from taking over. Although this website has scammed a huge number of people and any actors not arrested after this action will just move to another spoofing service this is good to see

 Any LE action is positive. Disruption is key to preventing fraud and scams from taking over. Although this website has scammed a huge number of people and any actors not arrested after this action will just move to another spoofing service this is good to see
Any LE action is positive. Disruption is key to preventing fraud and scams from taking over. Although this website has scammed a huge number of people and any actors not arrested after this action will just move to another spoofing service this is good to see
 I am worried about the SMS alerting, it's a great idea in concept but sending an SMS with a link is the same technique threat actors use.
Potentially an SMS alerting a victim and asking them to go to the site as opposed to adding a link might be a better technique
I am worried about the SMS alerting, it's a great idea in concept but sending an SMS with a link is the same technique threat actors use.
Potentially an SMS alerting a victim and asking them to go to the site as opposed to adding a link might be a better technique
 I can see this potentially being abused by fast thinking actors, although they only have 2 days to action their scam. However how many people will know that the police are only sending texts for 2 days?
I can see this potentially being abused by fast thinking actors, although they only have 2 days to action their scam. However how many people will know that the police are only sending texts for 2 days?  One other highly notable part of this reporting is the Dutch polices malware implant on the websites server. This is offensive blue teaming at its best
One other highly notable part of this reporting is the Dutch polices malware implant on the websites server. This is offensive blue teaming at its best
It's great to see law enforcement taking proactive steps to enrich their investigations by hijacking websites to gather evidence to take down key players as opposed to just taking down the domain name or host

This is disruptive take downs and has multiple other places where this kind of deep action could take place. It's key moving forward to preventing fraud as opposed to playing whack-a-mole all the the with scammers 

 The ispoof website is now sitting on IP 66.212.148.115 which also hosts a number of with seized websites controlled and taken down by LE such as z-lib[.]org, kickass[.]to and pfizermx[.]com
The ispoof website is now sitting on IP 66.212.148.115 which also hosts a number of with seized websites controlled and taken down by LE such as z-lib[.]org, kickass[.]to and pfizermx[.]com
I hope you learnt something from this thread 
 Follow me for more #Phishing News Analysis and the Latest #Phishing IoCs
Back to the top?
twitter.com/JCyberSec_/sta
Follow me for more #Phishing News Analysis and the Latest #Phishing IoCs
Back to the top?
twitter.com/JCyberSec_/sta

 Follow me for more #Phishing News Analysis and the Latest #Phishing IoCs
Back to the top?
twitter.com/JCyberSec_/sta
Follow me for more #Phishing News Analysis and the Latest #Phishing IoCs
Back to the top?
twitter.com/JCyberSec_/sta
Jake | JCyberSec_@JCyberSec_
Nov 24 22
View on Twitter
 UK police to send 70,000 SMS after taking down ispoof
The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc
UK police to send 70,000 SMS after taking down ispoof
The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc Full Details and Analysis in Thread
Full Details and Analysis in Thread

Thread by @Jake | JCyberSec_ on Thread Reader App threadreaderapp.com/thread/1595715

Jake | JCyberSec_
@JCyberSec_
Expert in Credential Phishing and Phishing Kit Research.
Working in Cyber Security - Threat Intelligence
#Phishing
Missing some tweets in this thread? Or failed to load images or videos? You can try to .




![@JCyberSec_: ⚠️UK police to send 70,000 SMS after taking down ispoof The UK’s largest fraud operation has brought down a phone number spoofing and OTP capturing site - ispoof[.]cc📱 Full Details and...](https://pbs.twimg.com/card_img/1595716538027352066/sIFyZsaW?format=jpg&name=orig)