Corben Leo@hacker_
Nov 25, 2022
8 tweets
I hacked a phone company earlier last year.
I found a stupidly simple way to view the call logs of 50M customers.
Here's how I did it:
1/ I've been in this bug bounty program for quite some time.
I previously bought a phone plan so I could login and test functionality as an authenticated user.
In the dashboard, there was a tab to view your call logs.
2/ The URL contained a parameter called "subscriberId".
It contained a numerical ID, so obviously I tried to change it to another users.
Unfortunately, it didn't work.
3/ After spidering the site with Burp, I eventually came across an old Javascript file.
This javascript contained a reference to a JSP file with a name that indicated similar functionality:
"/myaccount/modals/view_call_log_details_modal.jsp"
4/ So, I visited the endpoint:
███.com/myaccount/moda
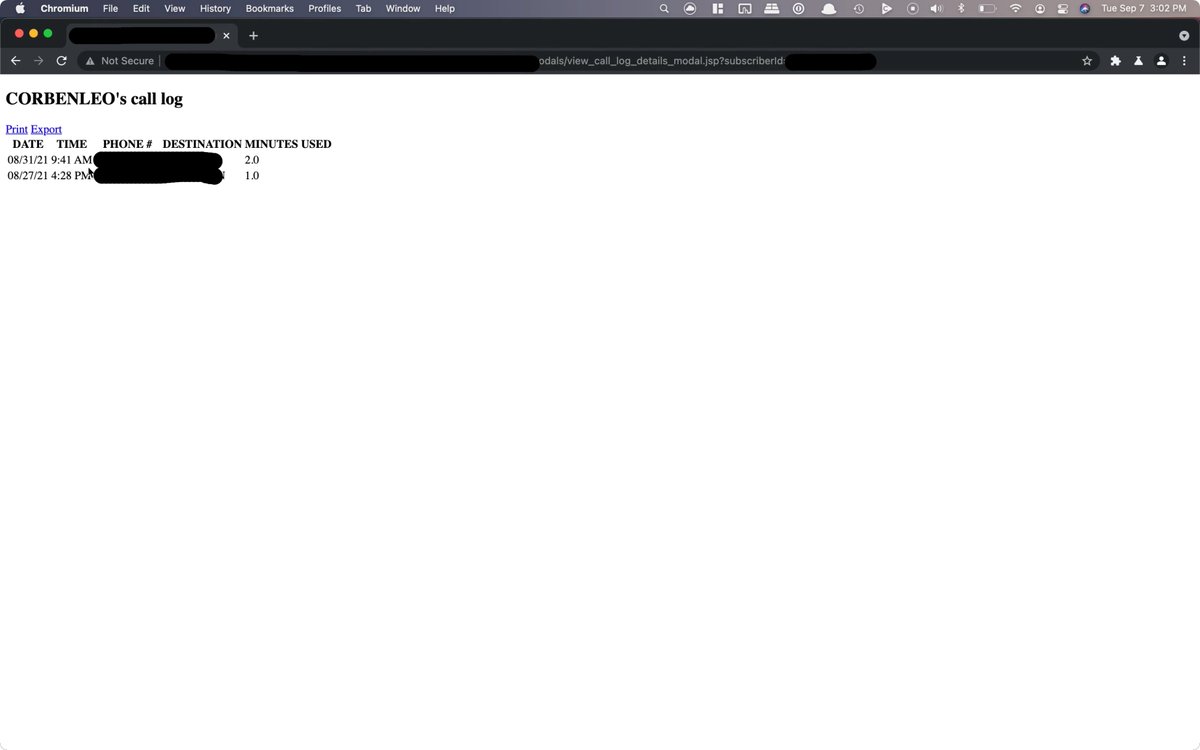
The page loaded, and in the response I saw my call logs:
Hm. What happens if I try to change the subscriberId to someone else's here?
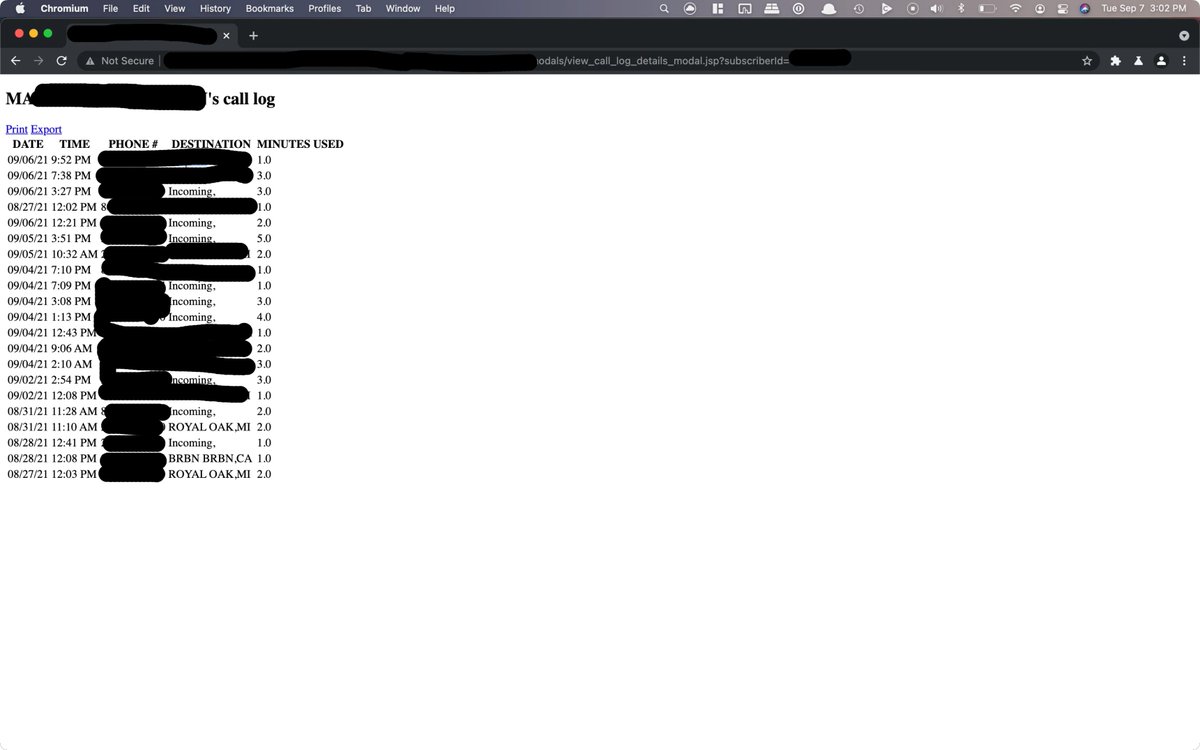
5/ I tried again, with another person's ID:
It actually worked.  An incredibly stupid, simple vulnerability affecting 50M+ customers. Insane
An incredibly stupid, simple vulnerability affecting 50M+ customers. Insane
 An incredibly stupid, simple vulnerability affecting 50M+ customers. Insane
An incredibly stupid, simple vulnerability affecting 50M+ customers. Insane 6/ I eventually found 5 other similar issues that leaked:
• Customer names, phone numbers
• Payment details (cards, amounts, dates of payments)
• Etc.
I reported them all to their bug bounty program and they duplicated them into one report and eventually fixed the issues.
7/ I'm still blown away that such simple, stupid vulnerabilities exist.
x.com/hacker_/status

Corben Leo@hacker_
Nov 25 22
View on Twitter
I hacked a phone company earlier last year.
I found a stupidly simple way to view the call logs of 50M customers.
Here's how I did it:
Missing some tweets in this thread? Or failed to load images or videos? You can try to .